
There has been an alarmingly incremental rising trend among threat groups these past years that have used seemingly legal means to obtain code signing certificates to sign their malware.
Mossé Security CSIRT team presents 15 malware examples signed by COMODO and used against Australian organisations:
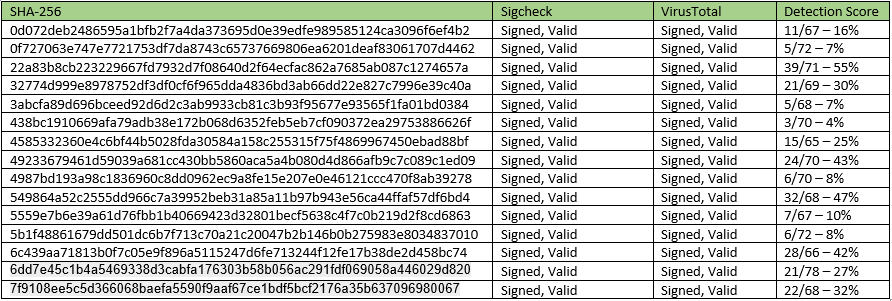
Each of these samples has a valid, legitimate signature. This demonstrates how successful the use of legally obtained code signing certificates have made rampant proportions easily attenable.
This alarming display as evidenced in the above information does prompt the question: How easy is it for adversaries to acquire a code signing certificate and sign their malware?
Our team of researchers here at Mossé Security conducted various experiments to discover the degree of rigorousness involved in the process of purchasing a digital certificate. A key process is illustrated further below.
From the significant number of online resellers of code signing certificates to choose from, our research team chose cheapsslsecurity.com. The initial application process to purchase the certificate was easy, straight forward, and posed no immediate roadblocks, as you will see in the sample below:
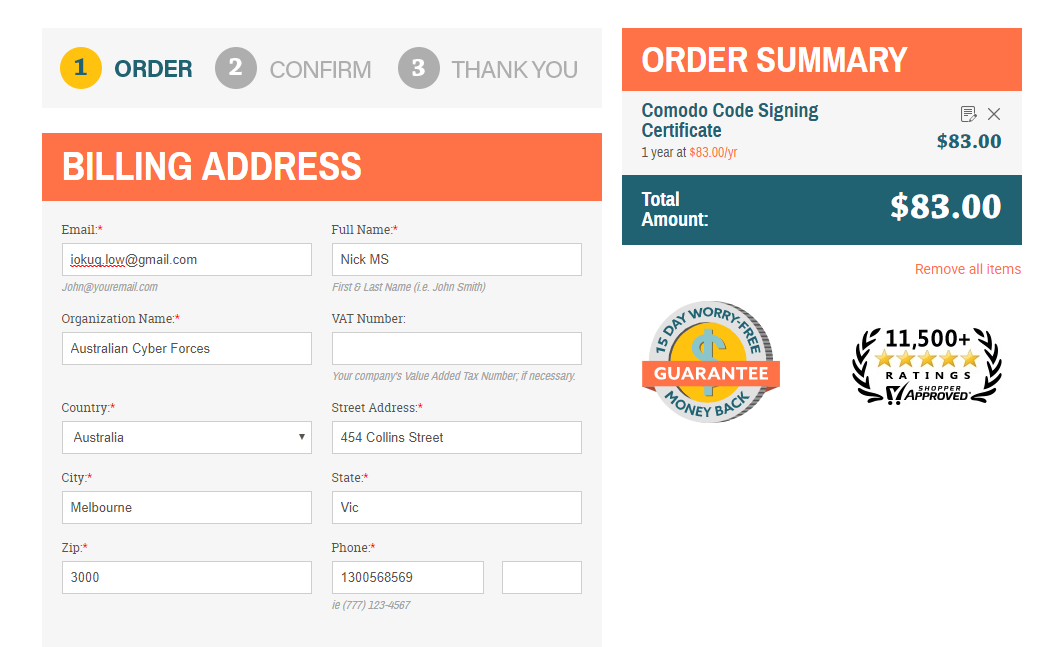
Surprisingly, payment method choices offered are Credit Card and Paypal, both easy to subvert.
After the order is placed, as well as the confirmation of payment method and payment authorisation is done, then the purchaser (adversary) creates an account. Thus begins the verification process based on which type of certificate was chosen – either “Individual” or ” Organisation”.
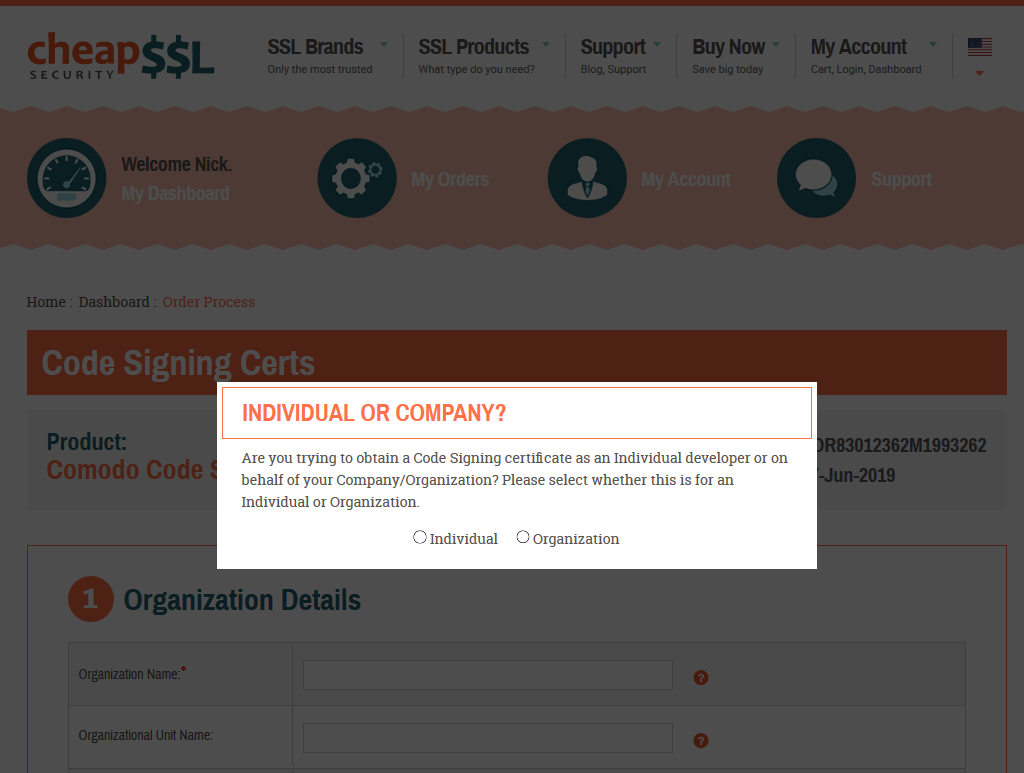
Our team of expert researchers found that the verification process is a more involved process than the registration, however, still allowing areas for subversion.
Out of the two options, “Organisations” demands more rigorous requirements, as shown in the examples below:
Prove that Your Business Exists: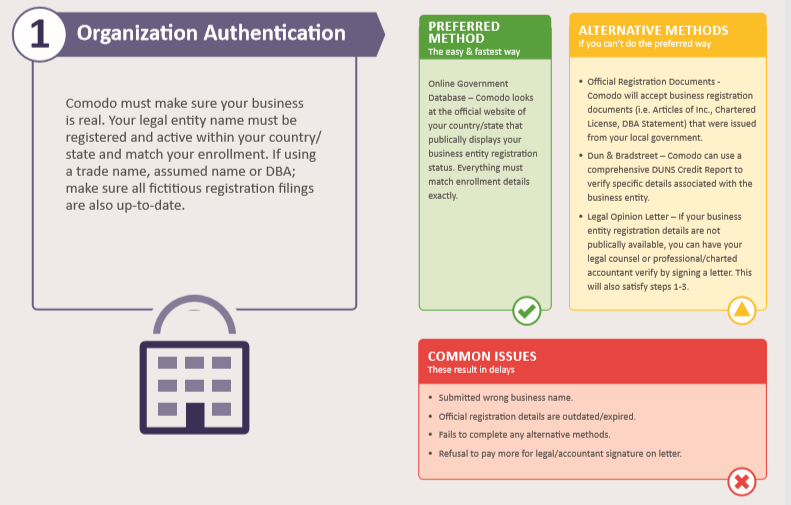
However, proving that the so-called organisation exists, requires little action from the applicant, as long as the information supplied corresponds to the information located in the country/state government database entry.
Alternatively, a signed letter from legal counsel or an accountant can suffice, as shown below:
Prove Physical Presence within Registry Country: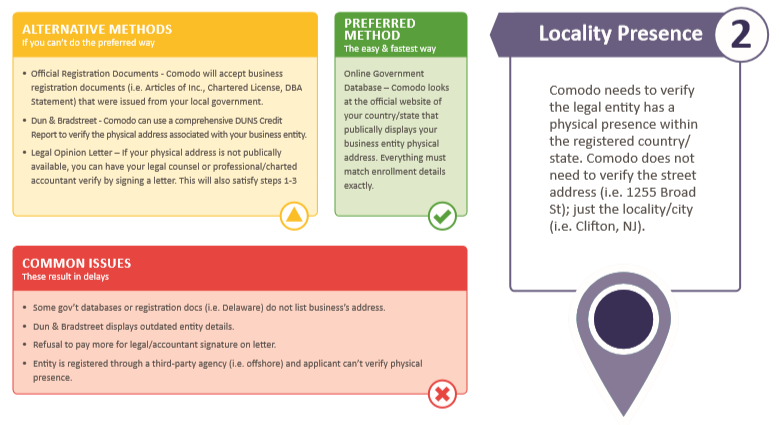
Similar to proving the existence of a said organisation, the address information needs only to match the one indicated in the country/state government database entry of the registered organisation.
Again, alternatively, a signed letter from legal counsel or accountant can suffice.
Telephone Verification: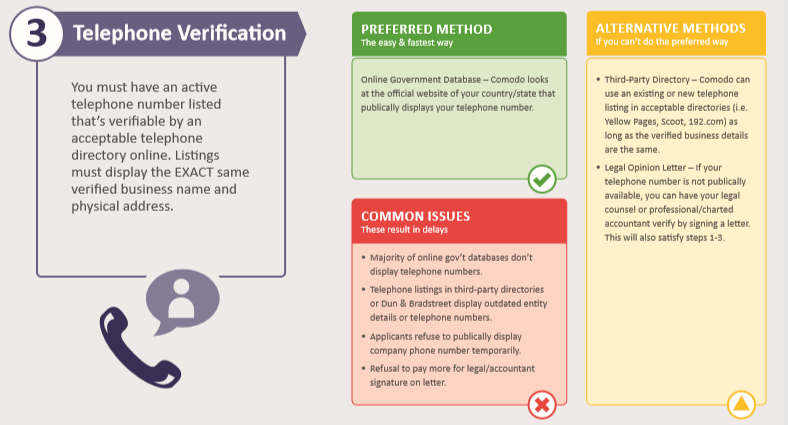
The indicated registered telephone number is checked against the country/state government database, or in a third party directory, such as Yellow Pages, Scoot, or 192.com. Alternatively, a signed letter from legal counsel or accountant can suffice.
Final Verification Call: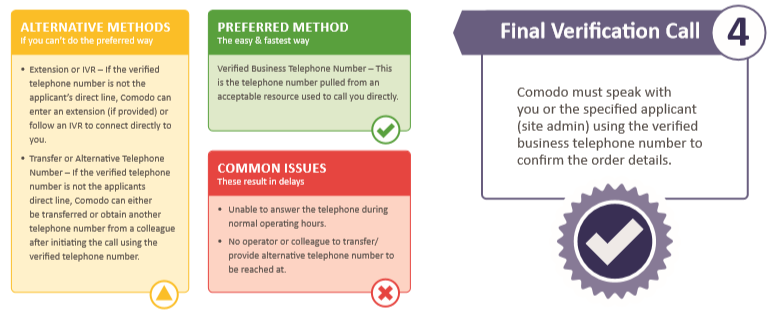
The final stage of verification is the most involved one, and it consists of a verification phone conversation from them to the registered phone number.
Applying for a certificate as an “Individual” is significantly easier process compared to the “Organisation” certificate.
Prove Your Identity: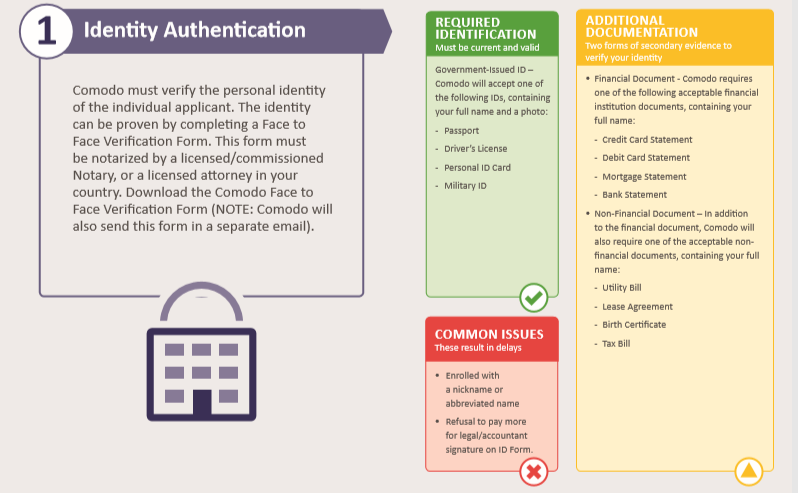
To prove your identity, all that is required is one of the following photo identifications:
Alternatively, two of the following non-photo identifications can be supplied:
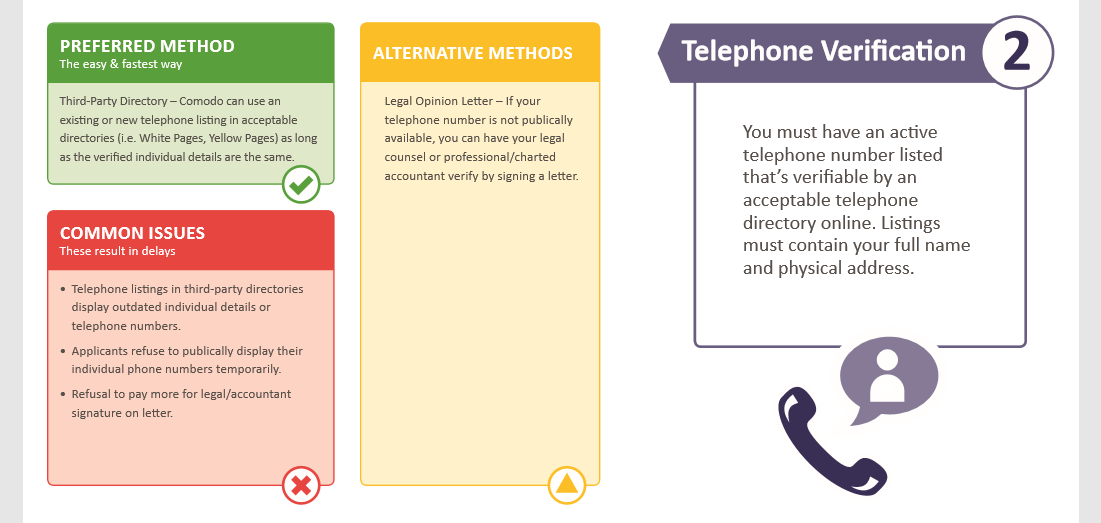
Similar to the process involved in verifying the registered phone number for Organisations, Individuals can be verified from a third party online director, such as White Pages or Yellow Pages,or with a letter from the individual’s legal counsel or professional accountant.
Final Verification Call: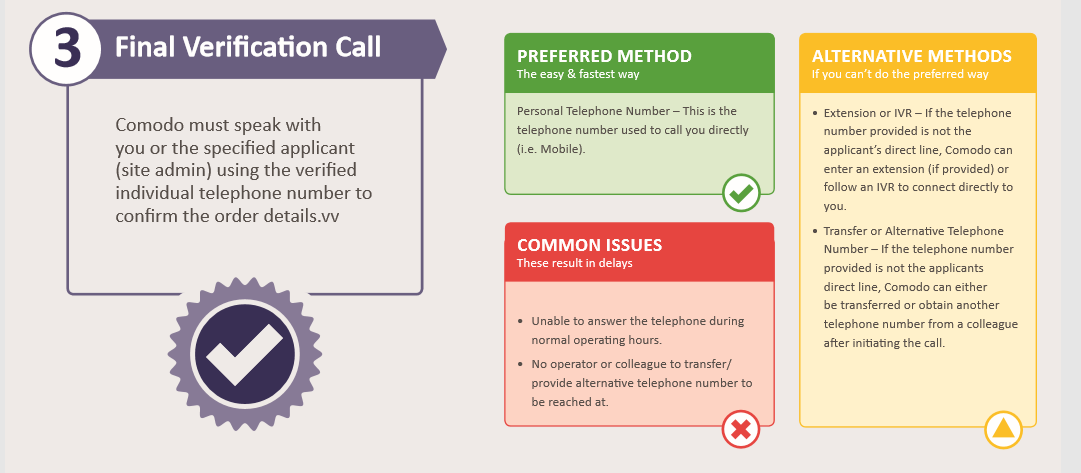
Similar to the Organisation application, a final phone conversation will be conducted from the registered phone number.
The experiment that our research team conducted concluded that the process of legally obtaining a code signing certificate for signing malware is a relatively easy one.
Mossé Security CSIRT has observed that time and time again, IT professionals will automatically rule out a suspicious Windows executable as a false-positive if it is signed. Digital signatures thus create a false sense of security that the adversaries can and do exploit to great success.
We hope that this article has served as an eye-opener to understanding the rampant nature of signed malware.