
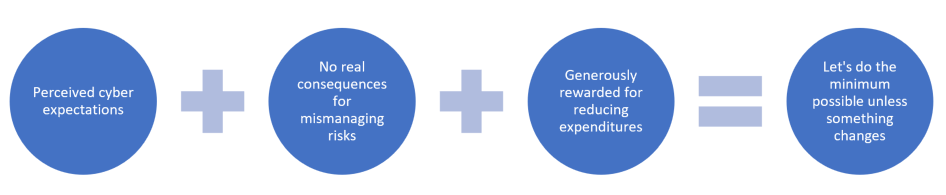
Business executives and managers are already aware that cyber security breaches can lead to financial losses, reputational damages, breaches of privacy and many other detrimental outcomes. Yet, as far as they’re concerned, the worst outcome that can happen to them personally in the catastrophic situation of a cyber breach, is an accusation of cyber security mismanagement leading to being fired.
They are not going to go to prison. No one is going to take their personal assets to reimburse the victim of the cybercrime.
Recommending and setting an ample budget on cyber security does not lead to any direct benefit to them personally. However, if they can save the company money, by either cutting expense corners or generating more money, then they’re rewarded with bonuses, awards and promotions. It naturally falls to ask ourselves if it’s even probable to achieve consistent cyber security outcomes if people face zero consequences for not delivering real security safety? We’ve had many opportunities to note that this operational ideology and concepts are fairly universal worldwide.
This widespread problem begs the question whether employees, at any level within any organisation, are even incentivised by their employer for actively and strongly expressing their inclination towards securing IT systems to protect company data. Given the somewhat incorrect belief that the cost of cyber security is “too high”, then the widespread tenet amongst companies who apparently are lacking in this sort of incentivisation, runs high, even though the company may belong to a community that deems cyber safety as important.
How do organisations meet their cyber obligations and expectations whilst avoiding the high cost of cyber security?
They use two business instruments:
Compliance and Risk Management were created by well-meaning people and institutions whose mission is to help organisations manage their cyber risk properly and provide guarantees to consumers and third parties.
Unfortunately, in the hands of people who are incentivised every day to save money and that view cyber security as a cost centre, Compliance and Risk Management have become the tools they use to pretend that they are meeting their community and legal expectations and keeping data safe.
The following case study has been anonymised to protect the parties. We at Mossé Security have witnessed hundreds of cases similar to this one, and readers will most likely have similar stories of their own.
Penetration testers were engaged to assess the security of a 3rd party application intended to hold personally identifiable information (PII) for tens of thousands of Australians. The purpose of the engagement was for the purchaser, who had already signed a contract with the vendor, to perform a last-minute due diligence activity. The IT manager and the CISO, however, had not been invited to participate in the procurement process, and therefore were unwilling to approve the solution without the penetration test performed first.
The penetration testers, within 8 hours of testing, identified 7 high-risk vulnerabilities that demonstrated that the vendor had not implemented any secure software development practices. All the major web application security controls (authentication, authorisation, session management etc.) had vulnerabilities.
Consequently, it was determined that in order to fix the root causes of all these security vulnerabilities, the vendor would need to spend at least $700K – an expense they were not prepared to absorb.
Several stakeholders had also set their minds on purchasing this application and having the vendor host it in their data centre (not the cloud) because:
Business question: $50K per annum, vs. $250K per annum, vs. $700K one-time - which one would you choose?
Once the penetration testing report had been issued to them and the findings were undebatable, the final decision-makers on cyber risks knew that it was not possible for them to ignore the issues.
They were not prepared to spend $250K per annum, or give the vendor $700K to fix the vulnerabilities permanently. Nor were they prepared to use another solution that may have been more secure but did not meet their business requirements.
Their solution was to hire an independent cyber-risk management consultant.
Here’s what the cyber risk management consultant came up with:
What was astutely and conveniently ignored?
By misusing “risk management” the organisation could now spend $15K per annum and produce all the paper trail needed to justify that it was managing its cyber risks appropriately.
Everybody involved in the discussions knew exactly what was being done. The IT manager, the CISO and everybody else also knew that if they attempted to block this approach from going ahead in anyway, then they would be labelled as “too difficult to work with”, removed from this project and prevented to fully engaging in any future cyber-security decision making.
The tens of thousands of individuals who have their personal data stored in that application are the biggest losers of this cyber security farce.
They are guaranteed to have their data stolen by cybercriminals sooner or later. These criminals will compromise this application or another one that’s been mismanaged in a similar way.
Fundamentally, cyber security costs too much and is still too difficult to implement. Even implementing the “basics” (however you wish to define that) is outside the capabilities and appetite of most organisations.
It’s easier and cheaper to manipulate the “compliance” and “risk management” business instruments rather than deliver real cyber security. Consumers and users are also not ready to pay for real cyber security.
The only way to solve this is to somehow make cyber security virtually free for everybody. This won’t happen anytime soon – if ever, as cyber security has its costs and is also too lucrative.
The government is not prepared to enforce stricter cyber security regulations in the private sector, the risk being an increase in the cost of doing business in Australia, which would further impact the nation’s ability to compete in the global marketplace.
Mismanaging businesses, from a cyber security perspective, is also not a criminal offense and perhaps may never be so.
As mentioned above, this is the case in almost every country. Australia is not being singled out.
If this article has raised questions you want answered for your organisation’s cyber security, then do call us to learn how we can help.
Benjamin Mossé
13/08/2019