
Mossé Security CSIRT observes signed malware used against Australian organisations daily.
Enterprise security products and IT professionals are advised not to automatically trust a file because it is signed. Digital certificates can be legitimately purchased for less than $100.00 USD. Adversaries also steal digital certificates from software vendors or extract certificates from legitimate binaries.
If your Red Team hasn't run an exercise of attacking your networks with signed malware, then we at Mossé Security strongly recommend that they do so. The results are likely to challenge many of the cyber defence assumptions made by the Blue Team and impart a trove of good lessons.
Our in-house analyst, Nick, presents further below, a case study using a free and open-source tool to sign malware samples. In this case, he could decrease detection rate by 21.9% against anti-virus engines available in Virus Total.
This tool has been available for anybody to download since 2017 and is still effective against many enterprise security solutions.
Casting our minds back to the 26th of September 2017, some of you may remember Casey Smith's following tweet:
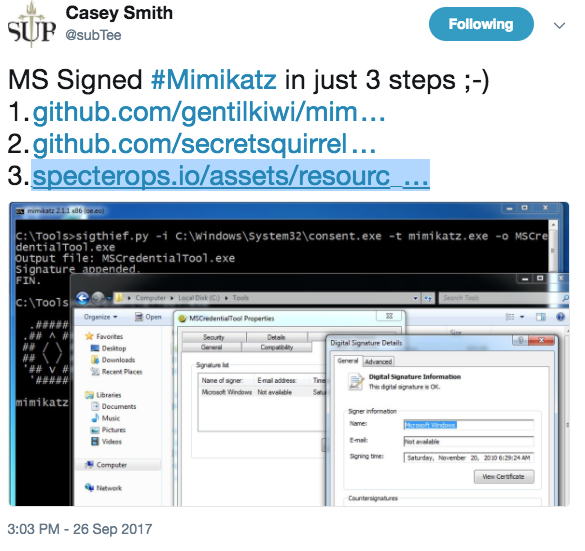
Using a 267-line Python script, Casey took the digital signature of consent.exe (a Microsoft-signed executable) and appended it to mimikatz.exe, a malicious penetration-testing tool by Benjamin Delpy.
On a recent engagement at one of our high-profile clients, our analysts wanted to test the signature detection and validation capabilities of their endpoint detection and response (EDR) solution.
The first test was a simple, low effort test, similar to Casey Smith's tweet ('exactly' is a more accurate term, as procexp64.exe was used to supply the signature).
The results were surprising.
Written by Josh Pitt aka “secretsquirrel” back in 2017, sigthief.py is a Python script that rips a digital signature of a PE (Portable Executable) and appends it to another.
This leaves the door wide open for any binary (including malware) to appear to be signed by a legitimate company such as Microsoft.
Of course, if the digital signature is properly validated against the said binary, then tools such as sigcheck.exe will raise an error message, but that is hardly a limiting factor as we will see.
SigThief.py is simple to use:
python.exe sigthief.py -i procexp64.exe -t mimikatz.exe -o microsoft_mimikatz.exe
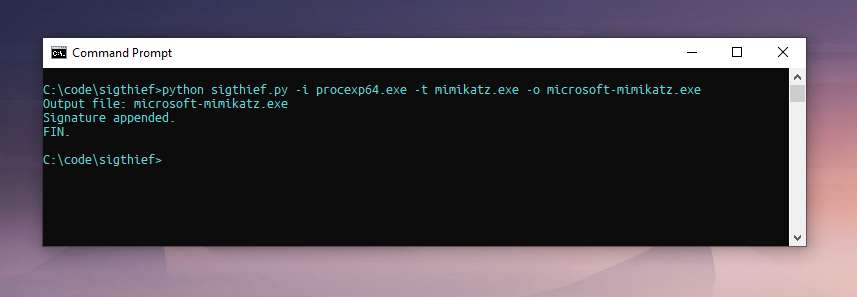
Using the -i flag, we can set the input file from where we want to steal the signature. The -t flag is used to set the target executable to append the stolen signature to. Finally, using the -o flag, we can set the output file.
Inspecting the digital signature properties of the output file we find that we have a copy of Mimikatz signed by Microsoft, unverified, of course.
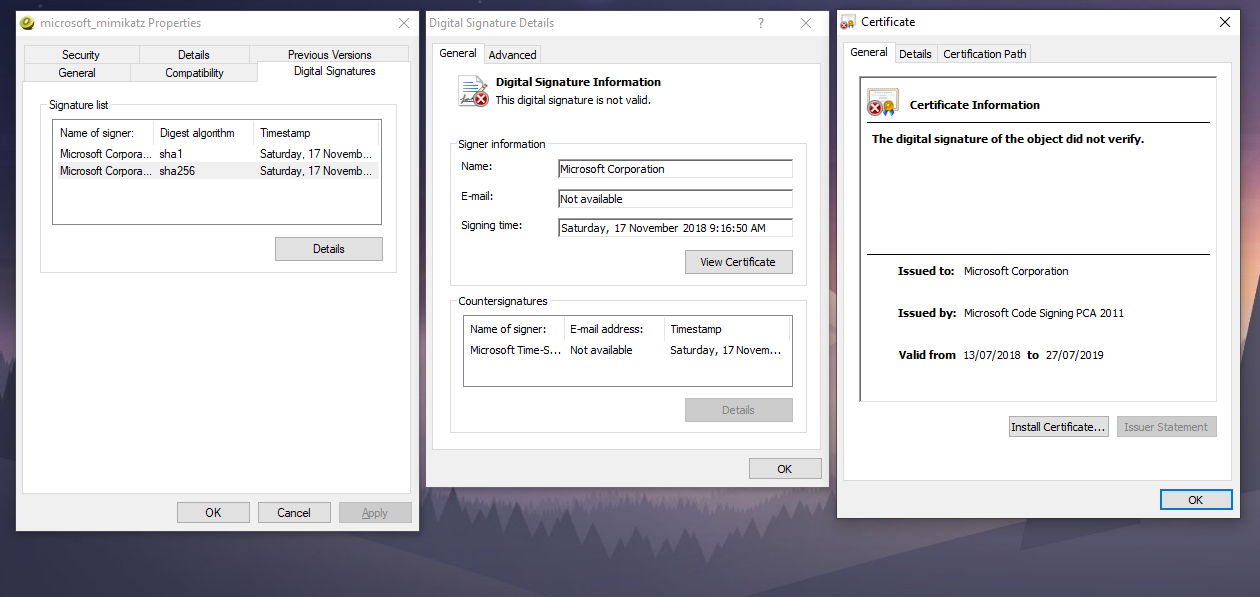
Here is where things get interesting.
Upon uploading our newly signed sample to Virus Total, it returned a detection score of 34/67:
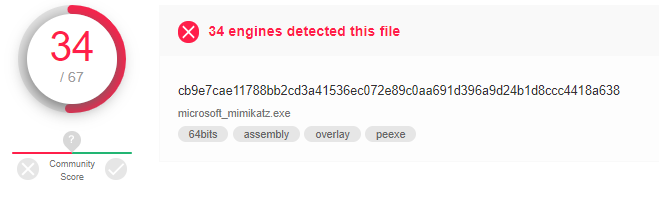
In comparison, the original, unsigned, version of Mimikatz that we based our sample on, returned a score of 53/72:
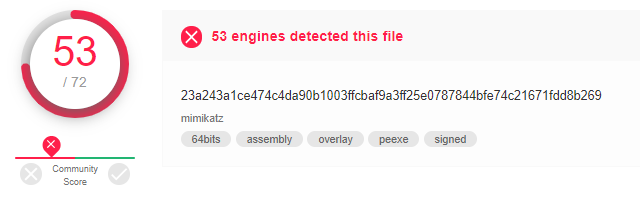
Mimikatz signed with Sigthief is detected by 50.7% of anti-virus and the unsigned Mimikatz is detected by 73.6% of the engines.
That's a difference of 21.9% in favour of the signed malware sample.
By performing a simple process that takes less than 2 minutes, we can reduce the probability of detection by almost 22%!
We leave it up to the reader to review the list of security products that were bypassed and draw their own conclusions…
Security analysts must accept that many commercial security products have a significant blind-spot when it comes to analysing files with digital signatures.
Attackers that sign their malware legitimately or use a tool like Sigthief can evade numerous endpoint security products because the malware generates automatic trust.
Anti-virus engines based on Machine Learning seemed particularly vulnerable to this defence evasion technique.
Worth noting as well is that YARA does not offer any capabilities to verify whether a PE's digital signature matches the file it's attached to or not.
Security analysts and system administrators investigating suspicious or unknown files would do well to not immediately assume that because a PE is signed then it's not malware.
Adversaries sign their malware all the time, and they also use tools such as Sigthief to defeat your anti-virus and EDR products, as well as static file analysis tools.
Published: 14/06/2019