
Mossé Security CSIRT has recently successfully responded to several breaches into corporate networks where the initial point of entry was a malicious portable application that provided reverse-shell capabilities to the adversaries.
Enterprise networks with thousands of employees will use a Standard Operating Environment (SOE) to harden the machines of employees.
In properly defended networks, the SOE will not allow employees to run unsigned executables or install new software, especially if that software was downloaded from an untrusted website. As a result, staff members that wish to use their corporate laptops for personal usage will download Portable Applications (PAs) to bypass security controls.
PAs provide a standalone, signed, executable to run software such as Firefox, Chrome, and VLC. They run out-of-the-box and do not require any installation.
Mossé Security CSIRT has identified adversaries that will compromise the developers of Portable Applications or subvert the submission process to publish a new PA as an indirect way to obtain unauthorised access into protected corporate networks where standard phishing and spear-phishing techniques do not work.
Australian organisations could be greatly impacted by this attack vector due to the large number of employees that use portable applications. In one network, we detected over 200 different portable applications being used.
As an example, consider this a malicious portable version of Mozilla Firefox seen in Australia:
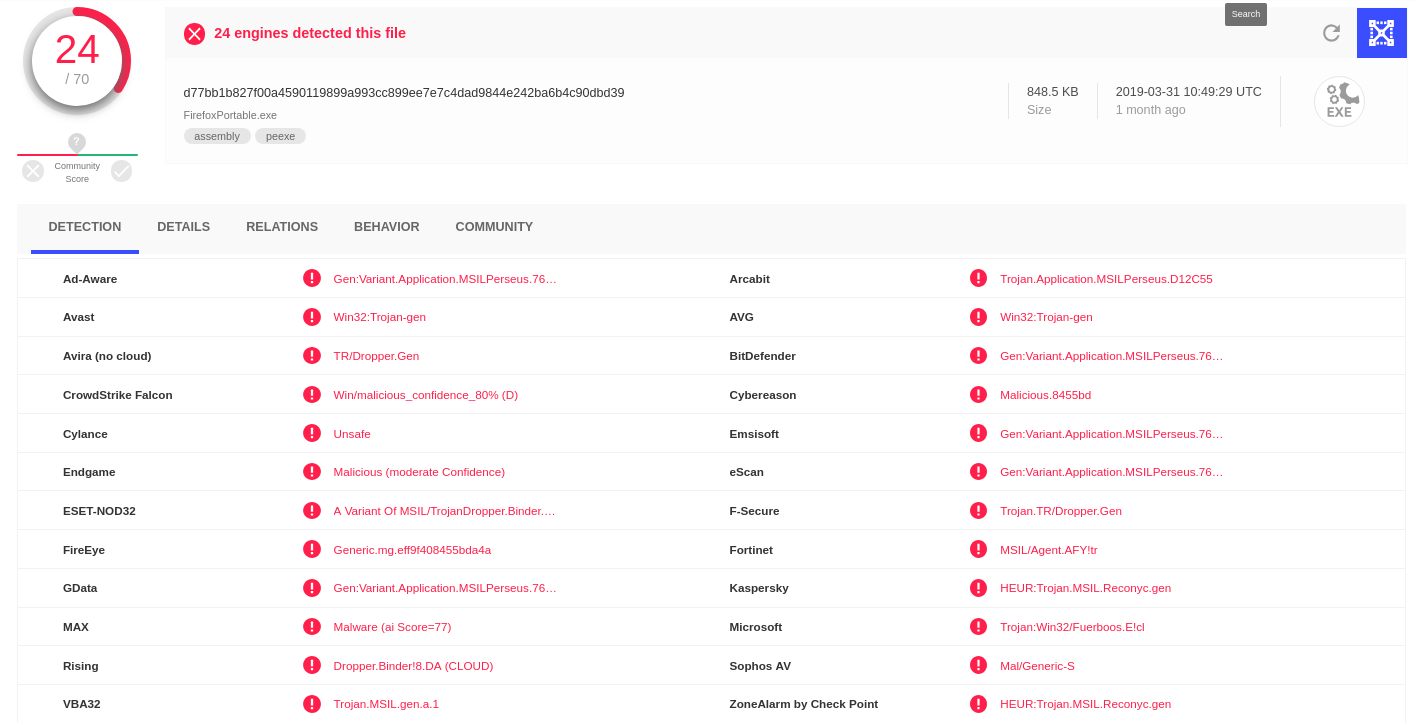
Figure 1: Screenshot from Virus Total of Mozilla Firefox Portable application displaying the results of which AV's were able to detect the file. source: https://www.virustotal.com/gui/file/d77bb1b827f00a4590119899a993cc899ee7e7c4dad9844e242ba6b4c90dbd39/detection
The following recommendations can be applied to limit and restrict usage of Portable Applications:
Implementing additional security restrictions in large-scale networks is not always the most viable approach. Hence, we recommend that you consider the following detection and response strategies as well:
Anti-virus software will protect against known malicious software but fail against never-seen-before binaries.
Using Portable Applications as an indirect way to breach into computer networks is another example of a supply chain attack. There is a growing trend of supply-chain attacks occurring worldwide that will continue because enterprises are largely unprotected, unaware, or unequipped to deal with that type of cyber risk.
Mossé Security has the advanced tools to identify, reverse-engineer, and hunt for any malware that have entered Australian organisations via supply-chain attacks. We recommend that Australian organisations, as well as worldwide ones, consider building partnerships with alternative trusted security vendors capable of identifying, reverse-engineer, and hunt for any malware that have entered their networks via supply-chain attacks.
In addition to our recommendations outlined above, our team has written a YARA rule to scan for portable applications residing on your networks. You may use it as well to block PAs using ProcFilter.
import "pe"
rule PortableApps {
strings:
$s1 = "CNET" ascii wide
$s2 = "PortableApps" ascii wide
$s3 = "Pendriveapps.org" ascii wide
$s4 = "TinyApps.org" ascii wide
$s5 = "Sourceforge" ascii wide
$s6 = "PortableFreeware.com" ascii wide
condition:
uint16(0) == 0x5A4D and pe.number_of_signatures > 0
and any of them
}
Published: 02/07/2019