
Recently, our analysts at Mossé Security have responded to several incidents involving several Australian corporate enterprises that have been aggressively targeted by APT groups in systematic social engineering campaigns, in an attempt to steal credentials. Many of these campaigns have been successful, resulting in the theft credentials belonging to a number of key, high-value employees from well-known retail businesses throughout Melbourne.
This report will focus on one recent campaign, carried out by a group we have labelled as "CRIME CHARLIE", offering details on their attack techniques as well as recommendations for protecting and mitigating against potential phishing campaigns.
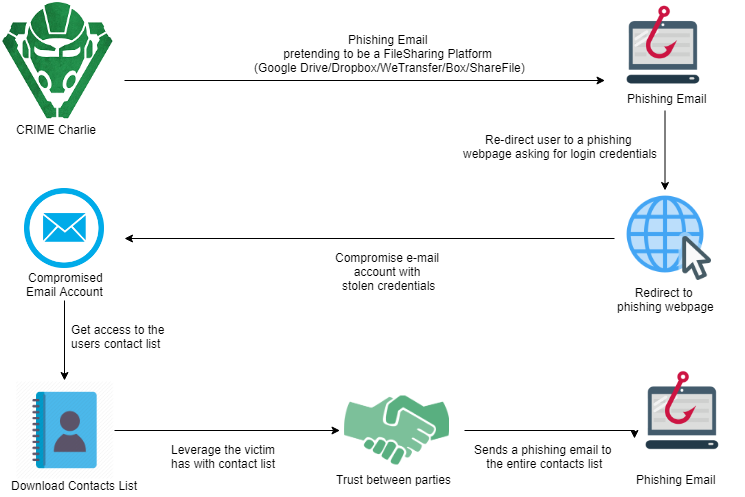
CRIME CHARLIE utilises carefully reproduced emails, based on invitation messages from cloud storage and file sharing companies such as Dropbox, WeTransfer, Google drive and the like. The emails link the target to a phishing login site, mimicking the look and feel of the legitimate company's site, where the user is instructed to 'sign in' to access the documents, harvesting their credentials. This action provides the adversary with access to contact lists as well as to a plethora of data that CRIME CHARLIE can weaponize for future campaigns.
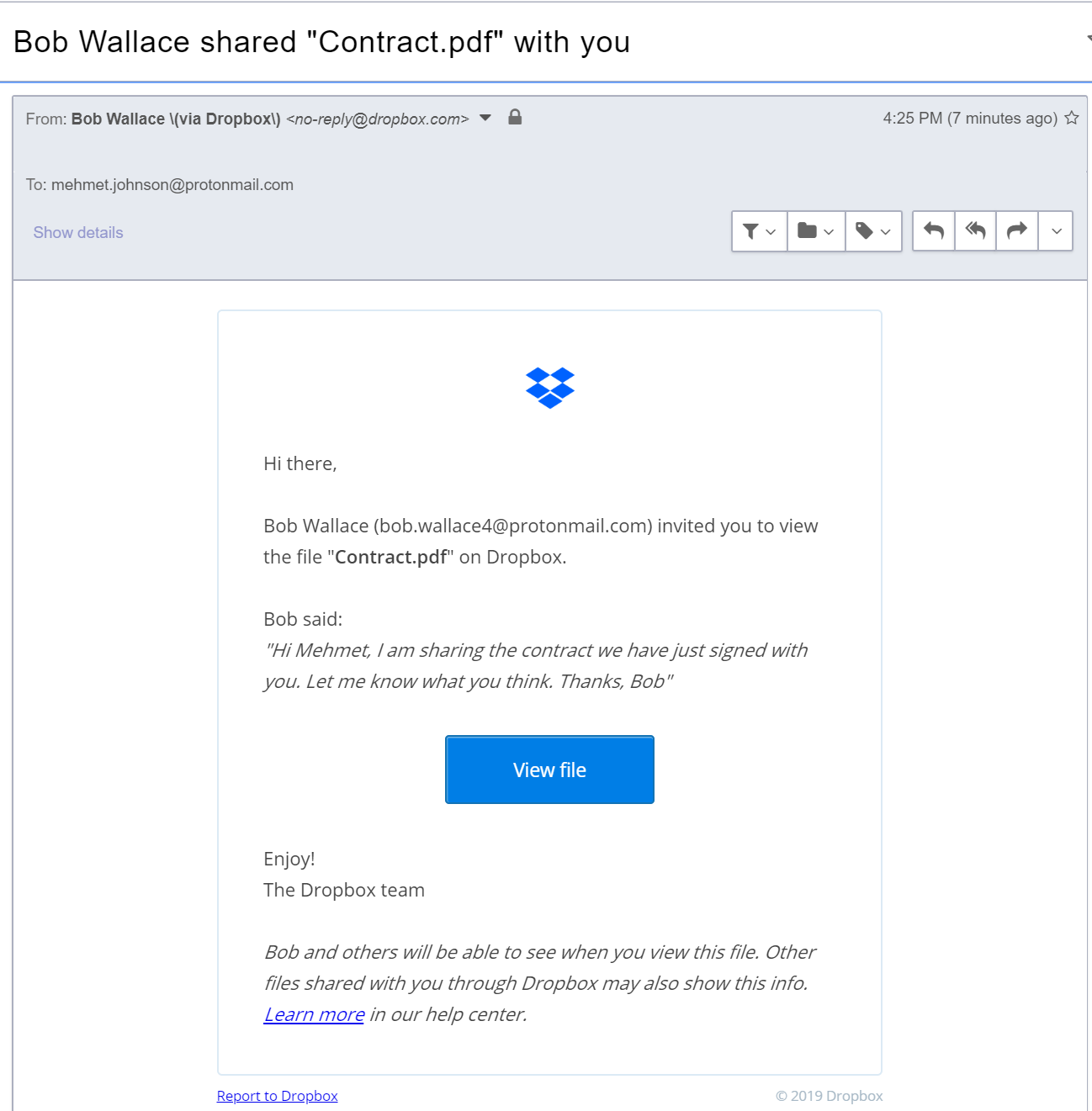
Dropbox is one of the most popular file-sharing platforms used in organisations worldwide with a free account easily registrable. However, if sharing files through Dropbox is common enough in an environment, employees are much more prone to trusting and being fooled by malicious ‘Dropbox’ emails. This is what makes this method highly successful.
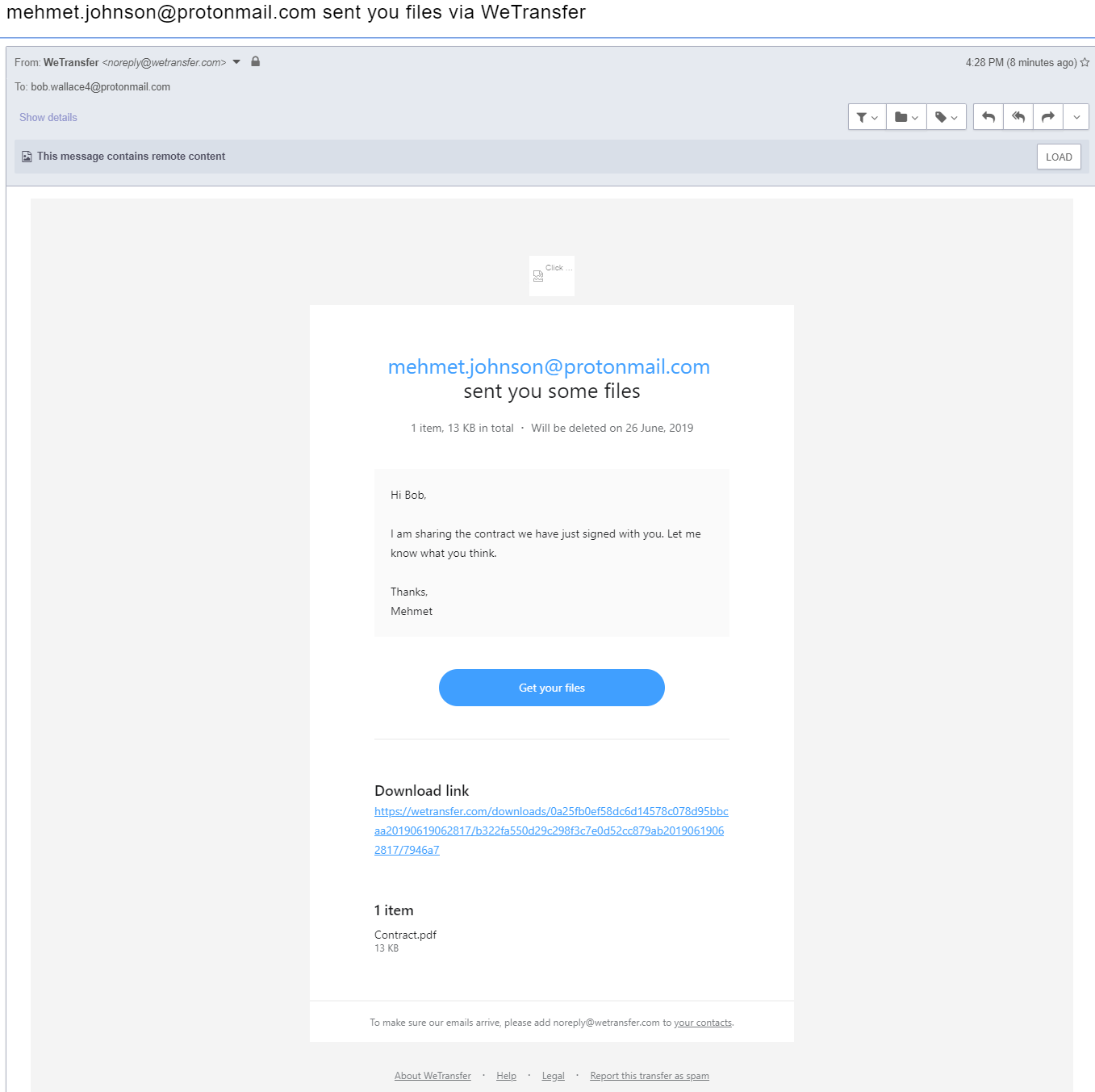
WeTransfer is a file-sharing platform, where a user can upload and distribute files to others without the need of an account. All that is required is an origin email, destination email, and a file to upload, as well as a short message (which is optional). We have observed WeTransfer becoming a common and popular alternative to file hosting/transfer solutions many enterprise environments have implemented.
At first glance, one may be tempted to dismiss an adversary like CRIME CHARLIE as script kiddies or opportunitistic adversaries that wouldn't cause too much damage.
This assessment would be incorrect.
CRIME CHARLIE's semi-automated phishing campaigns uses the email account of a compromised victim to phish all the contacts in his or her contact list, and repeats that pattern over and over again, compromising one organisation after another. As a result, organisations we've seen targeted by CRIME CHARLIE were subject to reputational damages, and in one case, a organisation had to notify over customers that their PII had been accessed without authorisation due to a cyber breach which in turn led to financial losses due to loosing customers.
Mossé Security also attributed several intrusions by other threat actors as a result of the network access first obtained by CRIME CHARLIE. We believe that the group steals credentials and then resells the information to other cyber criminal organisations on the Internet.
It's also unclear what other information CRIME CHARLIE downloads and steals from compromised email accounts, and what the impact of that breach could be for organisation over the long-term. It is very possible that CRIME CHARLIE sells corporate documents and intellectual property on the Dark Market.
Two-factor authentication is a method of confirming that user’s identity by combining something they know (password) and another factor, and often this 2nd factor would be something they have like a mobile phone. Two-factor authentication is important because if credentials are stolen by the threat actor, they still will not be able to gain access to the email account and when enabled makes you a lot harder to hack.
Recommendation 2: Restrict Usage of Unauthorised 3rd Party File Sharing ToolsEmployees often find a way to work around protocols and policies if something is more comfortable for them, or they prefer something different. Having a firm policy around file sharing is essential to ensure employees are keeping your organisation's documents secured. Part of creating a firm policy involves the organisation selecting one file-sharing platform to implement throughout the organisation and ensure staff use it. We recommend manually configuring firewalls and any proxy servers to ensure that any other file-sharing platforms are not allowed. As a result of these changes, employees will abide by the new policy.
Another component is creating a strong password policy to be implemented throughout the organisation ensuring that employees are using strong passwords, not using the same password on multiple sites, and using a password manager.
Recommendation 3: Security Awareness TrainingSecurity awareness training is used to help educate employees in the organisation to highlight the dangers of common online scams like phishing. Increasing your employee's education on cybersecurity and the types of attacks facing Australian organisations helps them to reduce errors, causing a breach and enhance your security.
CRIME CHARLIE is one of the more sophisticated groups of social engineers Mossé Security have responded to in Australia. Their techniques and tactics work against high-level personnel who have access to multiple areas of the business through their accounts and have interactions with valuable external clients.
CRIME CHARLIE does not go any further than email phishing from what we have discovered; they steal credentials from the organisation, then move onto the next target.
Many of the cybersecurity attacks we see have one element in common with them, the component of social engineering. Threat actors over time have begun to increase their social engineering tactics by using advanced techniques to trick victims into sharing sensitive information.