
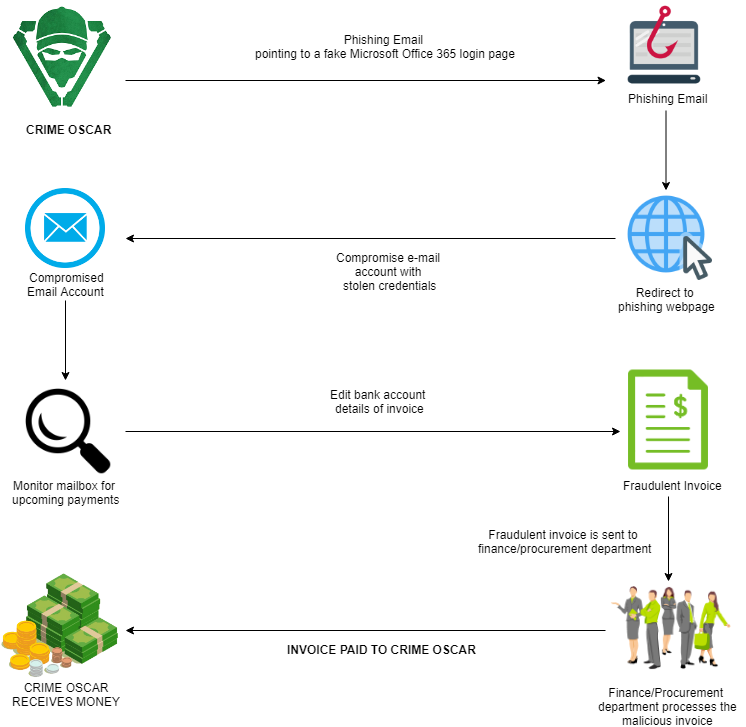
Mossé Security's CSIRT Team responded to several intrusions from a financially motivated threat actor we refer to as CRIME OSCAR.
Our CSIRT Team has successfully acquired the phishing toolkit used by CRIME OSCAR to carry out their attacks and have conducted a capability assessment on it. This Threat Report will breakdown this toolkit and its capabilities, highlighting how it was successfully used to steal multiple sets of credentials.
CRIME OSCAR uses their phishing toolkit to attack the finance/procurement departments of small to medium enterprises to alter invoices to their banking information for CRIME OSCAR to receive the payment. We have seen very ambitious financial amounts being requested in this manner to defraud organisations, with anywhere from between $50,000 to $2M.
As a result, victims of CRIME OSCAR were subjected to substantial financial damages.
The motivations of CRIME OSCAR are financial ones, as their goal is to compromise the mailbox of a member of the finance/procurement department using phishing and intercept upcoming payment invoices. Once a future payment is identified, CRIME OSCAR edits the banking details specified in the invoice to point to a mule, and then re-submits the invoice to trick the finance department into approving the new wire details.
Our CSIRT Team has responded to organisations targeted by CRIME OSCAR in the construction, mining and utility industries.
CRIME OSCAR gains access to organisation mailboxes using phishing techniques to steal login credentials by imitating login pages from Office 365. The phishing webpage loads up from CRIME OSCAR’s phishing toolkit, which they host one compromised Australian websites, providing an appearance that looks legitimate, in this way duping the victim to willingly enter their credentials.
CRIME OSCAR deployed their phishing tool on compromised websites with known PHP remote code execution vulnerabilities:
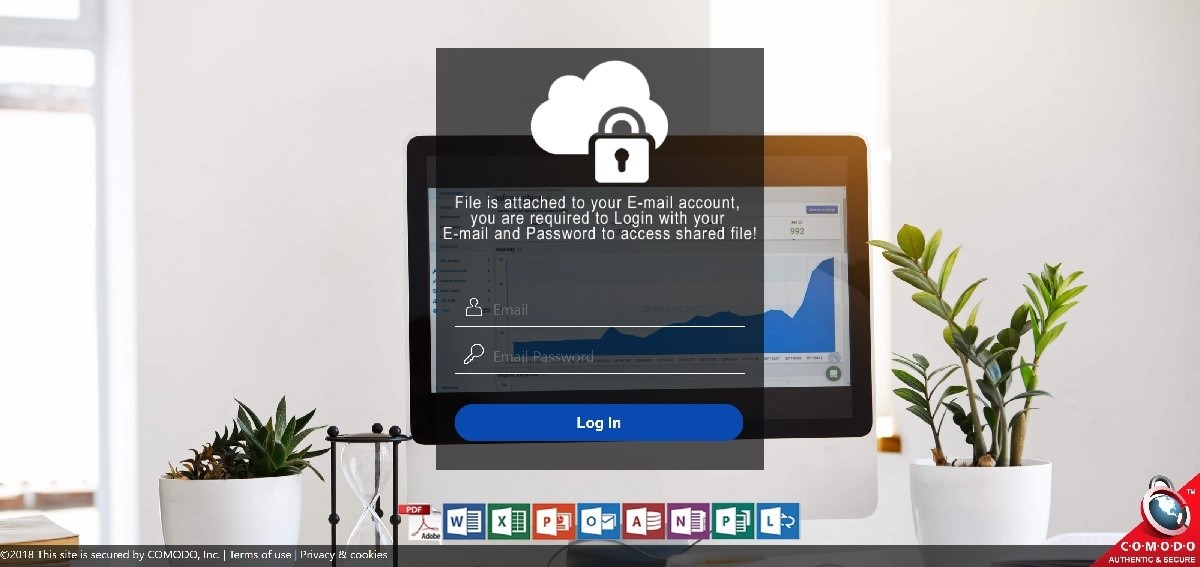
As seen from the screenshot above, CRIME OSCAR used a convincing login page that mimics the visual style of an Office 365 login page. CRIME OSCAR even goes as far as including fake certificate information (COMODO) in the bottom right corner of the page to reinforce an impression of legitimacy.
The form performs a simple input validation, ensuring that valid values populate both fields.
The phishing toolkit was written in PHP, presumably by a single author.
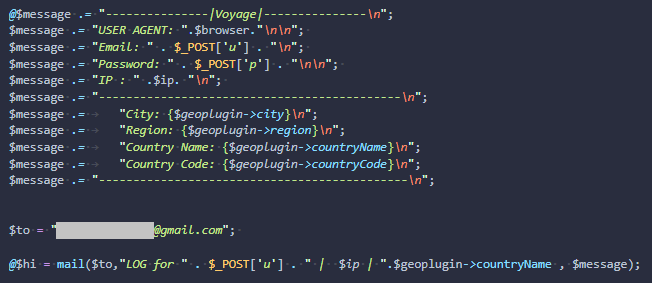
When a user submits their credentials then their username and password are sent to a hardcoded email address. Our CSIRT Team have identified several email addresses being used by CRIME OSCAR.
Once the credentials have been stolen, the victim/user is presented with an infinitely loading message saying, 'Retrieving file... Please Wait' page, giving the illusion that the victim/user has successfully logged in, and is experiencing a load error.
With two similar files used to exfiltrate the credentials - submit.php and submit1.php, it is worth noting the small difference between these two: submit.php is the one that accepts a phone number during one of the later stages of the process.
The toolkit sends credentials as soon as they are acquired and does not save the information on disk, making it impossible to ascertain which credentials the attacker has acquired without obtaining access to the email account used for collection.
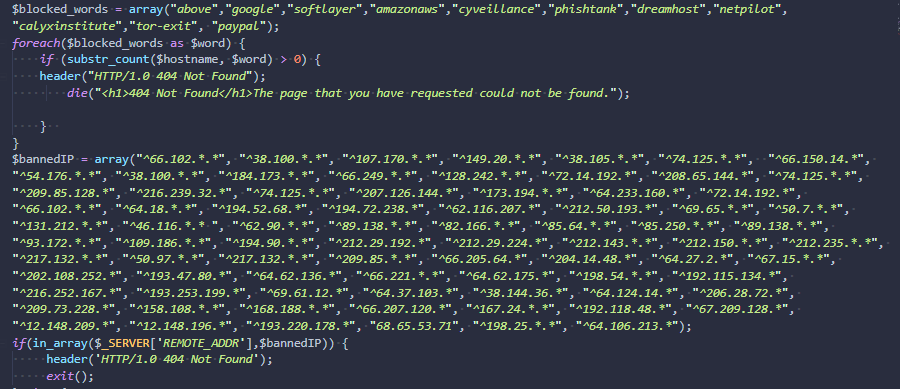
An interesting capability worth exploring is the toolkit’s OPSEC capabilities. The phishing framework checks the visitor’s IP address against a list of blacklisted IP ranges and addresses before rendering the pages and making the HTTP controllers available:
Run a mock-up incident simulation pretending that your organisation has been targeted by CRIME OSCAR. Demonstrate how you would do this:
Two-factor authentication is a method of confirming that user’s identity by combining something they know (i.e. their username and password) and another factor, and often a random code sent by text message to the user's mobile phone. Two-factor authentication is important because if credentials are stolen by the threat actor, they still would not be able to gain access to the email account, and even when enabled it would make it a lot harder to hack.
Recommendation 3: Security Awareness TrainingSecurity awareness training, such as the trainings offered by MSCI, is strongly recommended to help educate employees in the organisation, and to alert them to the value of getting a deeper understanding of the dangers of common online scams like phishing. Increasing your employee's education on cybersecurity and the types of attacks facing Australian organisations can help them reduce errors that could cause a breach. This would enhance your security by making each one adopting a sharpened sense owning cyber protection and safety.
The phishing toolkit employed by CRIME OSCAR is simple yet highly effective.
It utilises a convincing login page that evokes the look and feel of legitimate office login page and methods to ensure that correct credentials are harvested. Also, it contains OPSEC capabilities, designed to block untrusted visitors and possibly known security vendors. These elements combine to create a comprehensive and effective phishing tool, that has unsurprisingly proven to be very effective in the field.